- Support:+971 4 3364 840
- Email:[email protected]
- Locations:Dubai • Riyadh • Bangalore
Practice
Secure your Cloud. Focus on your Business.
Our premier managed security services specializes in comprehensive AWS cloud and hybrid infrastructure security. We safeguard your cloud perimeter, workloads, native applications, and serverless architectures with cutting-edge technology and expert oversight. We have partnered with Trend Micro, and use Trend Vision One platform as the core of our Managed Security Services program. Our 24×7 Security Operations Center (SOC) in Dubai Digital Park, in Dubai Silicon Oasis, UAE, ensure continuous monitoring, rapid threat detection, and immediate response. Trust us to fortify your AWS environment against evolving cyber threats, providing you with peace of mind and the freedom to focus on your core business operations.
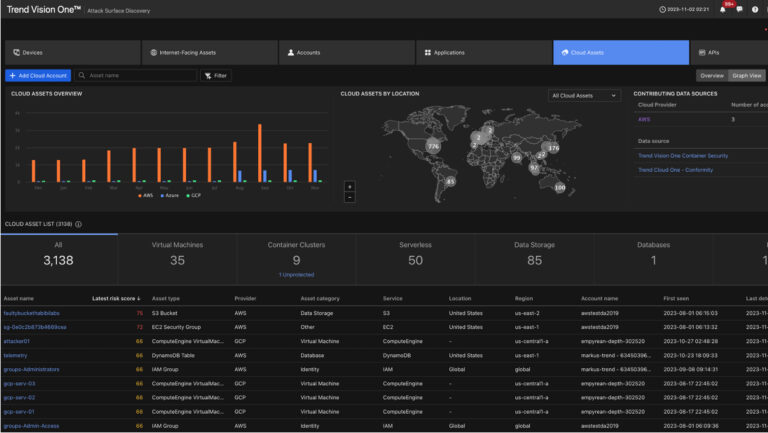
Routine scanning of AWS infrastructure resources for known software vulnerabilities. Newly added resources are automatically discovered and available for scanning. The AWS metadata for scanned AWS infrastructure is available as part of scan results to better enable reporting and decision making.
Continuous scanning and reporting of all AWS resources, and their configuration details, updated automatically with newly added or removed resources.
Detect when AWS accounts and the configuration of deployed resources do not align to security best practices.
What is the Trend Micro Vision One Platform?
How does MSS help?
24 x 7 Security
Our services do not just end with architecting secure solutions, they extend to 24/7 monitoring and response from our dedicated and specially trained security team. With detailed actionable insights obtained with our Trend Micro Vision One Platform, we are able to detect and contain threats immediately..
Regulatory Compliance
Meet your regulatory obligations with comprehensive security controls and unified reporting. Support for major compliance frameworks including PCI, HIPAA, and SOC2 ensures you're always audit-ready.
End to End Security
From AWS infrastructure to endpoints on cloud and on-premise, we secure every access point with tools from Trend Micro and other leading vendors, purpose-built for modern cloud and hybrid environments. A holistic approach to security ensures that no part is left behind.
Unified Security Platform
Monitor and manage security across your entire environment through a single pane of glass. Get comprehensive visibility into threats, vulnerabilities, and compliance status. Dashboards that can be customized according to roles.
How does it work?

Trusted by




